This maybe my last blog post about brontok as I think I had enough of it, I have just grab a copy of another brontok variant from my friend's network, coincidentally right after my post regarding brontok in last few days, lots of my friends calling me and telling that their "pc" infected by brontok. What I can say is that sorry I have no time to help you guys because I'm in busy state as well. Enough mumbling, back to the topic ....
This is not April Fool, yet I do like fooling people when I'm drunk or maybe being fooled .....
In the concept of Network Security Monitoring, collecting session data is a must. Though most people ignoring the role of it in security arsenal like I do few years back, but it is very useful when one involves in network security. There are few tools that considered in my favor list are ipaudit, argus and sancp which is used by Sguil project.
So how the hell session data will help in spotting worms? I will share a little knowledge of mine here. Before explaining about my finding, let's look at what is actually a computer worms. In wikipedia, a computer worm is a self-replicating computer program, similar to a computer virus. A virus attaches itself to, and becomes part of, another executable program; however, a worm is self-contained and does not need to be part of another program to propagate itself. They are often designed to exploit the file transmission capabilities found on many computers. The main difference between a computer virus and a worm is that a virus cannot propagate by itself whereas worms can. A worm uses a network to send copies of itself to other systems and it does so without any intervention. In general, worms harm the network and consume bandwidth, whereas viruses infect or corrupt files on a targeted computer. Viruses generally do not affect network performance, as their malicious activities are mostly confined within the target computer itself.
Computer worm replicates itself and try to propagate into or across the networks. Since it is written by human, it won't change by itself since it's behaviour has been predefined and programmed. Based on this fact, I believe that it is possible to spot worms by watching session data. Full content data needs to be collected if one want to analyze the payload, however the main point here is you may locate worms without even looking at anything by session data. I use brontok as experimental sampling. Here's what happen when I analyzed brontok inline with Sguil loaded in my VM at the same time. Snort generates alert on Netbios SMB Sessions. One of thing to be noticed is that the aggregate(CNT) of the event keeps increasing.
This is not April Fool, yet I do like fooling people when I'm drunk or maybe being fooled .....
In the concept of Network Security Monitoring, collecting session data is a must. Though most people ignoring the role of it in security arsenal like I do few years back, but it is very useful when one involves in network security. There are few tools that considered in my favor list are ipaudit, argus and sancp which is used by Sguil project.
So how the hell session data will help in spotting worms? I will share a little knowledge of mine here. Before explaining about my finding, let's look at what is actually a computer worms. In wikipedia, a computer worm is a self-replicating computer program, similar to a computer virus. A virus attaches itself to, and becomes part of, another executable program; however, a worm is self-contained and does not need to be part of another program to propagate itself. They are often designed to exploit the file transmission capabilities found on many computers. The main difference between a computer virus and a worm is that a virus cannot propagate by itself whereas worms can. A worm uses a network to send copies of itself to other systems and it does so without any intervention. In general, worms harm the network and consume bandwidth, whereas viruses infect or corrupt files on a targeted computer. Viruses generally do not affect network performance, as their malicious activities are mostly confined within the target computer itself.
Computer worm replicates itself and try to propagate into or across the networks. Since it is written by human, it won't change by itself since it's behaviour has been predefined and programmed. Based on this fact, I believe that it is possible to spot worms by watching session data. Full content data needs to be collected if one want to analyze the payload, however the main point here is you may locate worms without even looking at anything by session data. I use brontok as experimental sampling. Here's what happen when I analyzed brontok inline with Sguil loaded in my VM at the same time. Snort generates alert on Netbios SMB Sessions. One of thing to be noticed is that the aggregate(CNT) of the event keeps increasing.
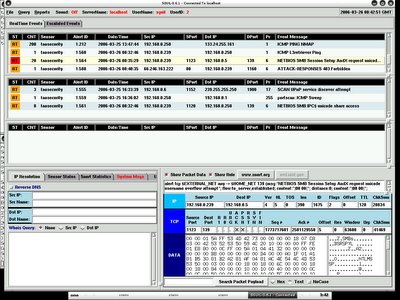
With sguil I can easily query the session data based on different criteria, below are the two screenshots that I have taken. If you have paid enough attention on source packet count and source bytes as well as destination packet bytes and destination bytes, you may find that the flow is always in the same sequence.
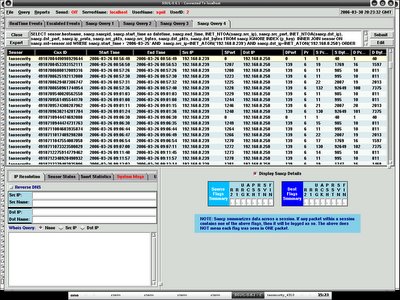

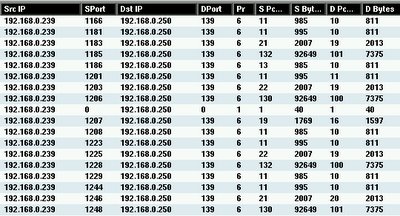
Here's the zoom in, so normally you will see the worm will try to ping(Pr equal to 1 which means ICMP and SPort + DPort = 0 since ICMP uses type and code instead of port) first to see if the host is alive and will try to connect to the IPC$ in order to access to victim's netbios share through port 139, and upload to the vulnerable host if there's any.
I generate the transcript of it with sguil, watching the conversation between them.
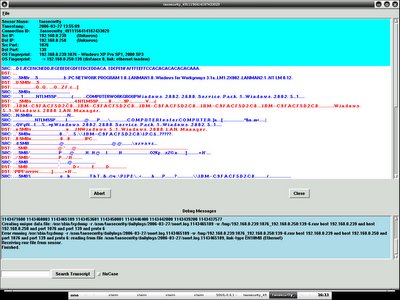
If I pull out the data using ethereal, everything will be much clearer and you may dissect everything that possible since ethereal is rich with it's decoder especially when you need to decode SMB/CIFS. However if you are analyzing it using tcpdump, you may need to run tcpdump with -vv option. Normally I use ethereal if I will have to examine full content data or learning protocols that I don't really much deal with.
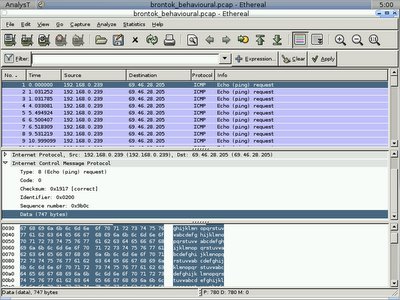
My main point here is if you notice or catch session data that goes with same sequence especially it's src packet count and length as well as dst packet count and length are always the same, then most properly your network is parasited by worm or it is in the wild. Computer worms normally has no intelligence to deal with this kind of detection since this is not signature base. One may consider writing worm that spreading with random junk data padded in the payload to confuse the security analyzt however that will only change the src packet bytes but dst packet bytes will still be the same since it is not controlled by worm. Another thing is the time interval may reveal the worms too because normally computer worm is built to spread in certain time period and not randomizing. Everything seems to be logical.
I really appreciate the value of session data not to say it is cheap to store but it is neutral to any kind of connection whether it is encrypted or not, as long as we records the connection pairs, we can learn and evaluate it later. Flow pattern tracking is real good in worm detection.
The screen below is not related to the title, I post it because someone ask me who is the papa of brontok, so here you have it.
I really appreciate the value of session data not to say it is cheap to store but it is neutral to any kind of connection whether it is encrypted or not, as long as we records the connection pairs, we can learn and evaluate it later. Flow pattern tracking is real good in worm detection.
The screen below is not related to the title, I post it because someone ask me who is the papa of brontok, so here you have it.
Though nowadays worm mostly getting through by email because they know human is the easiest to be cheated since there's no human firewall where cyber security is hardly taught and delivered. However flow pattern assessment is effective enough to detect worms in the LAN.
Just my little 2 cents, peace (:])
P/S: toxicle, I hope this is not april fool thingy :P, http://mydefcon.org .....
No comments:
Post a Comment